NETinVM
A tool for teaching and learning about systems, networks and security
| Authors: | Carlos Perez & David Perez |
|---|---|
| Date: | 2025-09-05 |
Introduction
NETinVM is a virtual machine image that provides the user with a complete computer network. For this reason, NETinVM can be used for learning about operating systems, computer networks and system and network security.
In addition, it can be used for demonstrations (i.e. in classrooms) that can be reproduced by students either in a laboratory or on their own laptop and thus, at home, at the library... For these reasons we present NETinVM as an educational tool.
Description of NETinVM
NETinVM is a virtual machine image that contains, ready to run, a series of Kernel Virtual Machine (KVM) virtual machines. When started, the KVM virtual machines create a whole computer network; hence the name NETinVM, an acronym for NETwork in Virtual Machine. This virtual network has been called 'example.net' and has fully qualified domain names defined for the systems: 'base.example.net', 'fw.example.net', etc.
Since NETinVM is a virtual machine and it contains other virtual machines, there are 2 virtualization levels. For this reason, the NETinVM virtual machine is called L1VM (level 1 virtual machine) and the internal KVM machines are called L2VM or KVM2 (for historical reasons).
All of the virtual machines use the Linux operating system. The L1VM is called 'base' and it runs Debian 12. KVM2 machines (L2VM) also use Debian 12 and they have different names depending on their network location, because they are grouped into three different subnets: corporate, perimeter and external. The subnetworks are named 'int' (for internal network), 'dmz' (for DMZ or demilitarized zone, usually used as a synonym for perimeter network) and 'ext' (for external network).
One of the KVMvirtual machine 2 machines, 'fw', interconnects the three networks ('int, 'dmz' and 'ext'), allowing for communication and packet filtering. The rest of the KVM2 machines have only one network interface, connected to the network they are named after:
- int<X>
- KVM2s connected to the internal network. <X> can take values from 'a' to 'f', both inclusive. These machines only offer SSH service by default.
- dmz<X>
KVM2s connected to the perimeter network (DMZ). They are supposed to be bastion nodes. Two preconfigured bastion nodes are provided, each one with its appropriate alias:
- 'dmza' is aliased as 'www.example.net' and it offers HTTP and HTTPS services.
- 'dmzb' is aliased as 'ftp.example.net' and it offers FTP.
- ext<X>
- KVM2s connected to the external network (ie: Internet).
Because a picture paints a thousand words, or so they say, the following figure shows NETinVM with all of the virtual machines running inside.
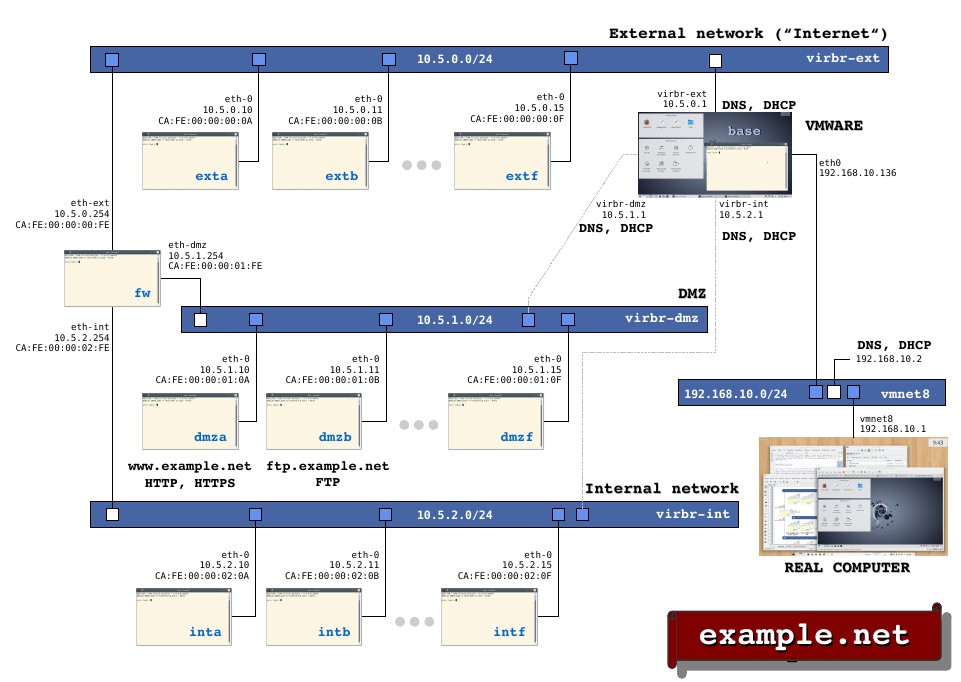
General view of NETinVM in VMware. The document example-net.pdf offers a detailed view.
All of the elements referenced before are shown in the image with their IP and ethernet addresses. The following rules have been used for assigning addresses:
- IP addresses are of the form 10.5.<NET>.<MACHINE>, where <NET> is either 0 ('ext'), 1 ('dmz') or 2 ('int'), and <MACHINE> is either 10 for 'exta', 'dmza' or 'inta', 11 for 'b' and so on up to 15 for 'f'.
- Network masks are 24 bits (255.255.255.0).
- Ethernet addresses are CA:FE:00:00:0<NET>:0<MACHINE>, where <NET> is either 0, 1 or 2 (following the same domain rule as IP addressing) and <MACHINE> is either a, b, c, d, e or f.
- The interfaces of 'fw' use 254 for IP and FE for ethernet.
- The interfaces of 'base' use 1 for IP and 01 for ethernet.
In addition to the computers and networks already described, the figure also shows the real computer where NETinVM runs ('REAL COMPUTER') and VMware Workstations's typical network interface ('vmnet8'), which optionally interconnects NETinVM's networks with the external word.
When they boot, all KVM virtual machines get their network configuration from 'base', which provides DHCP and DNS services to the three NETinVM networks through its interfaces 'virbr-ext', 'virbr-dmz' and 'virbr-int'.
Routing works as follows:
- The default gateway for the internal and perimeter networks (machines 'int<X>' and 'dmz<X>') is 'fw' (more specifically, the IP address of 'fw' in the corresponding internal or perimeter subnet).
- The default gateway for 'fw' is 'base' (its external network address).
- 'base' (its external network address) is also the default gateway for machines in the external network ('ext<X>'), but they are configured to use 'fw' (external network address) as the gateway for accessing machines in the perimeter and internal networks.
Thus, IP traffic exchanged among the three networks goes through 'fw', while traffic going out from NETinVM to the external world goes through 'fw' if (and only if) it comes from the internal or perimeter networks. All traffic going to the real world (outside NETinVM) exits through 'base' which, applies IP forwarding and NAT to this outgoing traffic, and routes it back through the external network using the routing table 'netinvm'.
Communication between 'base' and any KVM2 machine, in both directions, is direct, without going through 'fw'. (When the communication is started from a KVM2 machine, the IP address of the interface of 'base' in the corresponding network must be used.) This configuration permits access from 'base' to all KVM2 machines using SSH independently of the packet filtering configuration at 'fw'.
Working with NETinVM
Initial start up
To start NETinVM you need to download the VMware image, uncompress it and run it with the VMware Workstation program, which can be downloaded free of charge from VMware.
Once the VMware has been started, base.example.net is running, offering a standard KDE desktop for the unprivileged user user1. Its password is "You can change me.". The same password is valid for root, also. (The same users and passwords are also valid for KVM2 machines).
The idea is for base to be a desktop in which to work while doing exercises and that's why it includes LibreOffice and other similar tools. It is also designed to be the best place to monitor the traffic in the internal networks. To this extent, each network switch has a mirror port named after the corresponding network (mirror-ext, mirror-dmz and mirror-int). And base also includes wireshark and tcpdump. Other tools can, of course, be added by the user.
Graphical interface
NETinVM includes a "Folder View" component labelled "KVM machines" with graphical links to applications:
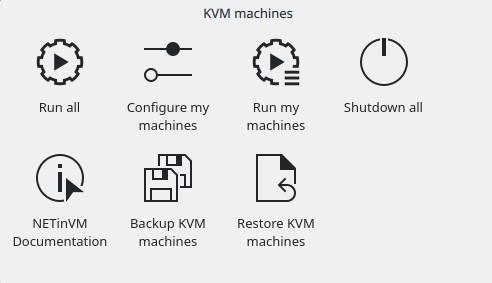
Links to applications to perfom most usual tasks with KVM2 machines.
When clicked on them, the links perform the following actions:
- "Run all"
- Brings to life NETinVM (see Full start up process).
- "Shutdown all"
- Shuts down all KVM2 machines.
- "Backup KVM machines"
- Creates a backup of the whole NETinVM network. (All machines must be shut down before backing up.) The backup is stored in a "tar.gz" file whose name can be set during the process. By default, backups are stored in "~user1/netinvm/backups" and are named "kvm_machines_yyyy-mm-dd_hh-mm.tgz", where "yyyy-mm-dd_hh-mm" stands for date (year, month, day of month) and time (hours, minutes).
- "Restore KVM machines"
- Deletes current KVM2 machine's state and restores a previous one. The backup file can be selected during the process. (All machines must be shut down before restoring a backup.)
- "NETinVM Documentacion"
- Launches a browser which shows a local copy of this documentation.
- "Configure my machines"
- Launches an editor to tune the script used by "Run my machines".
- "Run my machines"
- Brings to life the subset of KVM2s specified with "Configure my machines".
Full start up process
The command netinvm_run_all is the magic word that brings to life almost everything in NETinVM. Specifically, it launches the following elements:
- the virtual switches that make up the external (ext), internal (int) and screened (dmz) networks
- the KVM2 virtual machines: fw, exta, inta and dmza.
Although NETinVM is ready to run up to six KVM2 virtual machines per network ('a' through 'f'), with just the four mentioned above it is possible to develop a wide range of activities. Of course, in practice, the less KVM2 virtual systems running the faster the entire system will run.
Each KVM2 virtual machine starts up on a different KDE virtual desktop:
- exta on desktop 2
- fw on desktop 4
- dmza on desktop 5
- inta on desktop 8
On each desktop the following elements, all shown in the figure below, can be identified:
- A terminal window that, at the end of the booting process, allows the user to log into the KVM2 virtual sytem. It is the equivalent of a serial terminal hardwired to the KVM2 virtual system.
- Two more terminal windows which also work as terminals of the KVM2 virtual system, but start minimized.
Once all KVM2 virtual systems have been started it is easy to locate their corresponding windows by using the list of windows from KDE, which can be accessed by clicking on the "Window list" icon in the panel or pressing 'Meta-w'. The result should be similar to the following figure:

List of windows after all KVM2 virtual systems have been started.
All KVM2 virtual systems have an unprivileged user user1. The default password for both user1 an root in all KVM2 machines is (as with "base") "You can change me.".
Taking advantage of KVM and libvirt (or how to use the LXQT desktop in the KVM2s)
Although the KVM version of NETinVM has been designed to offer the same interface than previous NETinVM releases, this version uses libvirt. For this reason, NETinVM can also be used to learn about KVM and libvirt using online documentation.
In addition, the "virt-viewer" application can be used to launch a LXQT desktop in any of the KVM2 machines. For example, to start LXQT in "exta":
- Start "exta" using "Run all", "Run my machines" or by executing "netinvm_run exta".
- From a terminal in "base", as user "user1", run "virt-viewer --attach exta".
- In the graphical console launched by "virt-viewer", log in as "user1". (If the console is completely black, press ENTER to force a login prompt.)
- Run "startx".
- A full LXQT desktop should start after a few seconds.
Sample Exercises
The following documents describe some sample exercises that can be carried out using NETinVM.
Capturing an HTTP session with Wireshark
Capture an HTTP session from "exta" to "www.example.net" using Wireshark: Capturing an HTTP session with Wireshark.
Port Scanning with Nmap
Perform a full port scan against "www.example.net" from "exta.example.net": Port Scanning with Nmap.
Download information
NETinVM can be downloaded directly from its main page: index.html